
The Roundsec specialists managed to demonstrate the current zero-day vulnerability (0-day exploit) in the plugin of the popular CMS Magento.
This vulnerability is widely exploited by attackers from the Magecart consortium in a series of attacks on various services and platforms to steal users’ bank cards.
According to the cybersecurity sources, Magecart’s activity dates back to 2015 at least, and includes several criminal groups, using roughly the same types of attacks on CMS.
In 2018 the website of the British Airways company was compromised by the attackers with the help of this vulnerability. All users who made reservations through the company’s official website or app in the period between August and September 2018 were at risk. As a result of the breach, the personal data of 380,000 people (including their financial data) fell into the hands of the attackers. More information about this high-profile event can be found at the link https://www.riskiq.com/blog/labs/magecart-british-airways-breach/
Also, in 2018, this vulnerability affected the Feedify service. This service allows site administrators to embed push notifications into their resources by integrating Feedify JavaScript libraries into the site code. The first who noticed the compromise was an information security specialist, known on Twitter under the nickname Placebo. He reported that one of the company’s JavaScript files (feedbackembad-min-1.0.js) contains the malicious code that steals users’ payment data.
Magecart on Feedify. A customer engagement tool. According to there website 4000+ website use there tooling/code. Fixed today after I notified them.@ HYPERLINK «https://twitter.com/ydklijnsma?ref_src=twsrc%5Etfw»ydklijnsma @GossiTheDog pic.twitter.com/K2czXkUoHD
— Placebo (@Placebo52510486) September 11, 2018
In August 2018, another high-profile attack was performed on the website of a major retailer Newegg. Hackers had been stealing the details of users’ bank cards for quite a long time. It is not known exactly how many users were the victims of the attack, but according to SimilarWeb, Newegg traffic reaches about 50 million visits per month.

The example of the malicious code for the theft of user’s credit card data:

Immediately after the attack was revealed, the company warned its users about the compromise.
Since all the above-mentioned attacks of this kind are directly related to the Magento platform, let’s make it clear how attackers compromise the CMS in such different cases. As you might guess, the answer is simple – they use breaches in plugins.
Experts from Roundsec have analyzed the vulnerable area of the code in detail. The error occurs due to the incorrect processing during the object serialization.
According to the OWASP Top Ten, in the critical risk ranking of web application the eighth position is occupied by the drawbacks of deserialization of untrusted data. This vulnerability has the identifier CWE-502 and lies in the fact that the application deserializes data from an untrusted source without their sufficient validation. As a result of an attack on deserialization mechanisms, a hacker often gets the opportunity to remotely operate commands in a compromised system.
Serialization is the representation of specific structures and objects of the programming language in a single format, usually as a line of a specific format or a sequence of bytes.
Deserialization is the reverse process: restoring structures and objects from a serialized line or a sequence of bytes.
Serialization and deserialization are often used to save the state of a program, for example, on disk or in a database, as well as to exchange data between different applications.
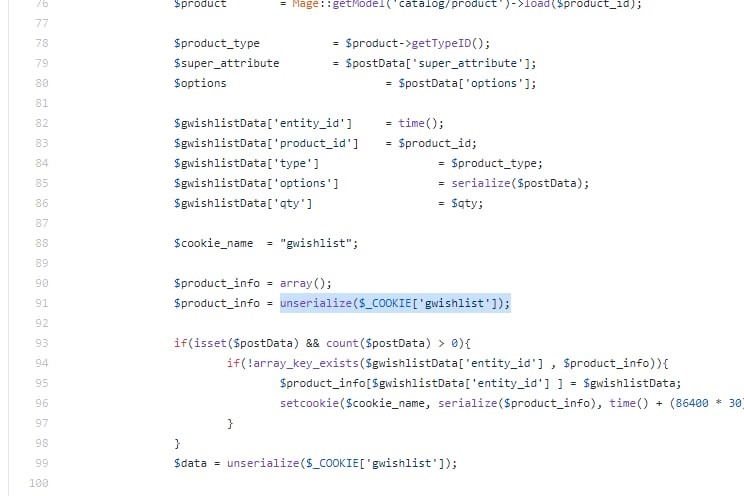
We located a section of code through which the attack can be performed.
Serialisation in PHP via the unserialise() method results in vulnerabilities that open access for hackers via RCE (remote code execution). Even in the absence of RCE, there is a possibility of bypassing the authentication system and implementing SQL code.
To test this vulnerability, specialists of the company set up a testbed and installed a dangerous plugin:
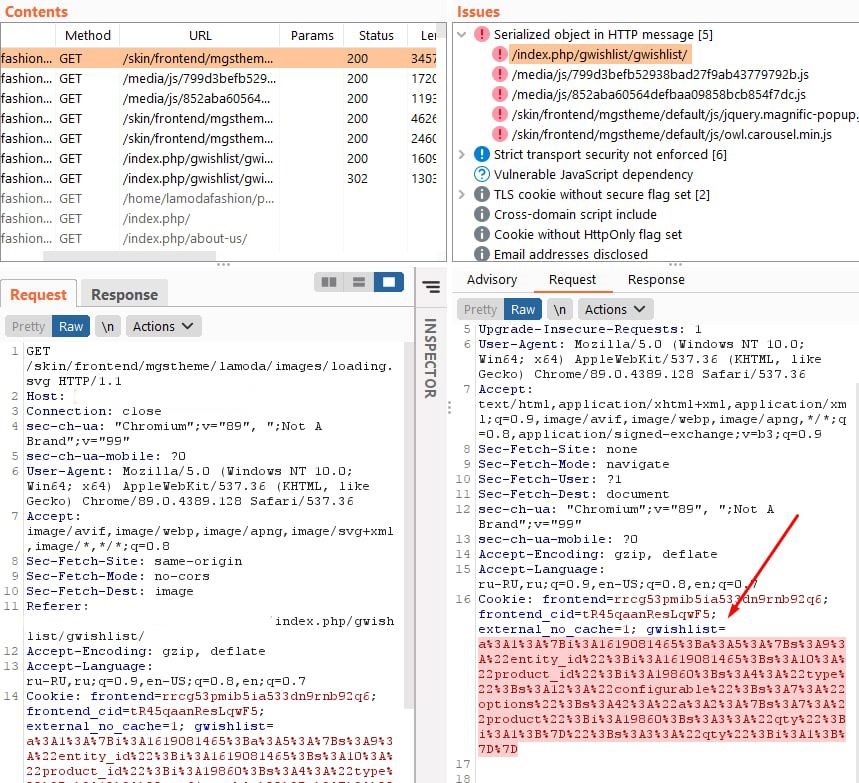
The vulnerability scanner detected a potentially dangerous vulnerability and issued a warning.
Accordingly, replacing Cookie with an additional parameter for executing the system command, we get RCE:

Successful execution of the RCE code. The vulnerability is detected.
To keep your data safe, do not neglect the security of the system and perform an audit and comprehensive review of the site at least 2 times a year. These and related services are provided by the specialists of our company Roundsec.
Share on social media
Want to discuss your project?
Fill out the form and our managers will advise you for free.


